Kubernetes基於helm安裝 harbor
之前harbor的安裝都是藉助docker完成一鍵安裝部署,安裝完成之後harbor元件均執行到一臺機器上面,本文實踐harbor在k8s環境中的部署。
準備工作
根據harbor官方要求:
- Kubernetes cluster 1.20+
- Helm v3.2.0+
結合ingress-nginx版本要求,建議K8S版本大於1.21.0-0進行實踐。
部署一套K8S環境
本文使用的k8s環境如下:
# k8s版本及環境資訊
root@master1:~# kubectl get node -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
master1 Ready control-plane 25h v1.28.2 192.168.0.61 <none> Ubuntu 24.04 LTS 6.8.0-36-generic containerd://1.7.12
node1 Ready <none> 25h v1.28.2 192.168.0.62 <none> Ubuntu 24.04 LTS 6.8.0-36-generic containerd://1.7.12
node2 Ready <none> 25h v1.28.2 192.168.0.63 <none> Ubuntu 24.04 LTS 6.8.0-36-generic containerd://1.7.12
# 作業系統資訊
root@master1:~# cat /etc/issue
Ubuntu 24.04 LTS \n \l
root@master1:~# uname -a
Linux master1 6.8.0-36-generic #36-Ubuntu SMP PREEMPT_DYNAMIC Mon Jun 10 10:49:14 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
# helm版本
root@master1:~# helm version
version.BuildInfo{Version:"v3.15.2", GitCommit:"1a500d5625419a524fdae4b33de351cc4f58ec35", GitTreeState:"clean", GoVersion:"go1.22.4"}
部署openebs用於提供pv
參考我的另外一篇文章部署openebs,《Kubernetes雲原生儲存解決方案openebs部署實踐-3.10.0版本(helm部署)》
本文部署的openebs資訊如下:
root@master1:~# helm ls -n openebs
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
openebs openebs 1 2024-07-02 14:38:40.928808834 +0800 CST deployed openebs-4.0.1 4.0.1
root@master1:~# kubectl get pod -n openebs
NAME READY STATUS RESTARTS AGE
openebs-localpv-provisioner-6b8bff68bd-vmwp7 1/1 Running 0 121m
openebs-lvm-localpv-controller-778b75449c-mmvw6 5/5 Running 0 121m
openebs-lvm-localpv-node-d2trc 2/2 Running 0 121m
openebs-lvm-localpv-node-md5wh 2/2 Running 0 121m
openebs-zfs-localpv-controller-6665568c7c-snw4q 5/5 Running 0 121m
openebs-zfs-localpv-node-mc8tv 2/2 Running 0 121m
openebs-zfs-localpv-node-w6nns 2/2 Running 0 121m
root@master1:~# kubectl get sc -n openebs
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGE
openebs-hostpath openebs.io/local Delete WaitForFirstConsumer false 121m
部署ingress-nginx用於暴露服務
參考我的另外一篇文章部署ingress-nginx,《ingress-nginx部署(helm方式)》
建議k8s版本不要太老,以下是在1.18.0部署最新的ingress-nginx,提示版本不相容。
[root@k8s-master ~]# helm upgrade --install ingress-nginx ingress-nginx/ingress-nginx \
> --namespace ingress-nginx --create-namespace \
> --set controller.service.type=NodePort
Release "ingress-nginx" does not exist. Installing it now.
Error: chart requires kubeVersion: >=1.21.0-0 which is incompatible with Kubernetes v1.18.0
本次環境部署的ingress nginx如下:
root@master1:~# helm ls -n ingress-nginx
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
ingress-nginx ingress-nginx 1 2024-07-01 18:20:48.811046861 +0800 CST deployed ingress-nginx-4.10.1 1.10.1
root@master1:~# kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-controller-dddq8 1/1 Running 1 (126m ago) 22h
ingress-nginx-controller-p7gd9 1/1 Running 1 (126m ago) 22h
部署harbor--ingress方式暴露服務
新增harbor helm倉庫:
helm repo add harbor https://helm.goharbor.io
官方提供四種方式暴露Harbor service:
- Ingress: 藉助Ingress暴露服務,K8S叢集中已經部署ingress nginx controller。
- ClusterIP: 使用ClusterIP暴露服務,只能在叢集內部進行訪問。
- NodePort: 使用NodePort暴露服務,透過NodeIP:NodePort進行訪問。
- LoadBalancer: 使用雲供應商提供的LB進行訪問。
部署harbor倉庫,使用ingress暴露服務。ingress-nginx使用的是NodePort方式暴露自身,需要在externalURL中配置其 NodePort 埠號:
# ingress-nginx NodePort https埠為30294
root@master1:~# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.230.242 <none> 80:30974/TCP,443:30194/TCP 21h
ingress-nginx-controller-admission ClusterIP 10.110.51.58 <none> 443/TCP 21h
# 檢視部署openebs後storageclass為openebs-hostpath
root@master1:~# kubectl get sc
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGE
openebs-hostpath openebs.io/local Delete WaitForFirstConsumer false 99m
# 執行helm安裝,指定為ingress暴露,指定域名,externalURL,密碼及StorageClaas
helm upgrade --install harbor harbor/harbor --namespace harbor --create-namespace \
--set expose.type=ingress \
--set expose.ingress.className=nginx \
--set expose.ingress.hosts.core=harbor.test.com \
--set expose.ingress.hosts.notary=notary.test.com \
--set externalURL=https://harbor.test.com:30194 \
--set harborAdminPassword="Harbor12345" \
--set persistence.persistentVolumeClaim.registry.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.jobservice.jobLog.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.database.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.redis.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.trivy.storageClass="openebs-hostpath"
檢視部署後的資源:
# 建立的pod
root@master1:~# kubectl get pod -n harbor -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
harbor-core-fb5ff9588-b8t6t 1/1 Running 2 (13m ago) 15m 10.244.154.33 node1 <none> <none>
harbor-database-0 1/1 Running 0 15m 10.244.154.43 node1 <none> <none>
harbor-jobservice-85bf44bd57-5f2wg 1/1 Running 6 (12m ago) 15m 10.244.154.41 node1 <none> <none>
harbor-portal-7c5d84cbb8-t6v22 1/1 Running 0 15m 10.244.154.34 node1 <none> <none>
harbor-redis-0 1/1 Running 0 15m 10.244.154.39 node1 <none> <none>
harbor-registry-7f54fbf5f4-xdx4t 2/2 Running 0 15m 10.244.154.42 node1 <none> <none>
harbor-trivy-0 1/1 Running 0 6m1s 10.244.154.45 node1 <none> <none>
# 建立的pvc
root@master1:~# kubectl get pvc -n harbor
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
data-harbor-redis-0 Bound pvc-83f38659-8ddb-43ec-9023-460d323c7d48 1Gi RWO openebs-hostpath 6m52s
data-harbor-trivy-0 Bound pvc-50b8cd59-23c3-4d15-a0e3-31b7a62ed5d5 5Gi RWO openebs-hostpath 6m51s
database-data-harbor-database-0 Bound pvc-8e8d04f2-21f7-4228-b0e7-331f352606e6 1Gi RWO openebs-hostpath 6m52s
harbor-jobservice Bound pvc-beca09bd-d3b7-4d82-8e1e-785de4728f4e 1Gi RWO openebs-hostpath 6m52s
harbor-registry Bound pvc-cd7048f3-2452-44e2-8c84-337b22ccb4ed 5Gi RWO openebs-hostpath 6m52s
# 檢視ingress
root@master1:~# kubectl get ingress -n harbor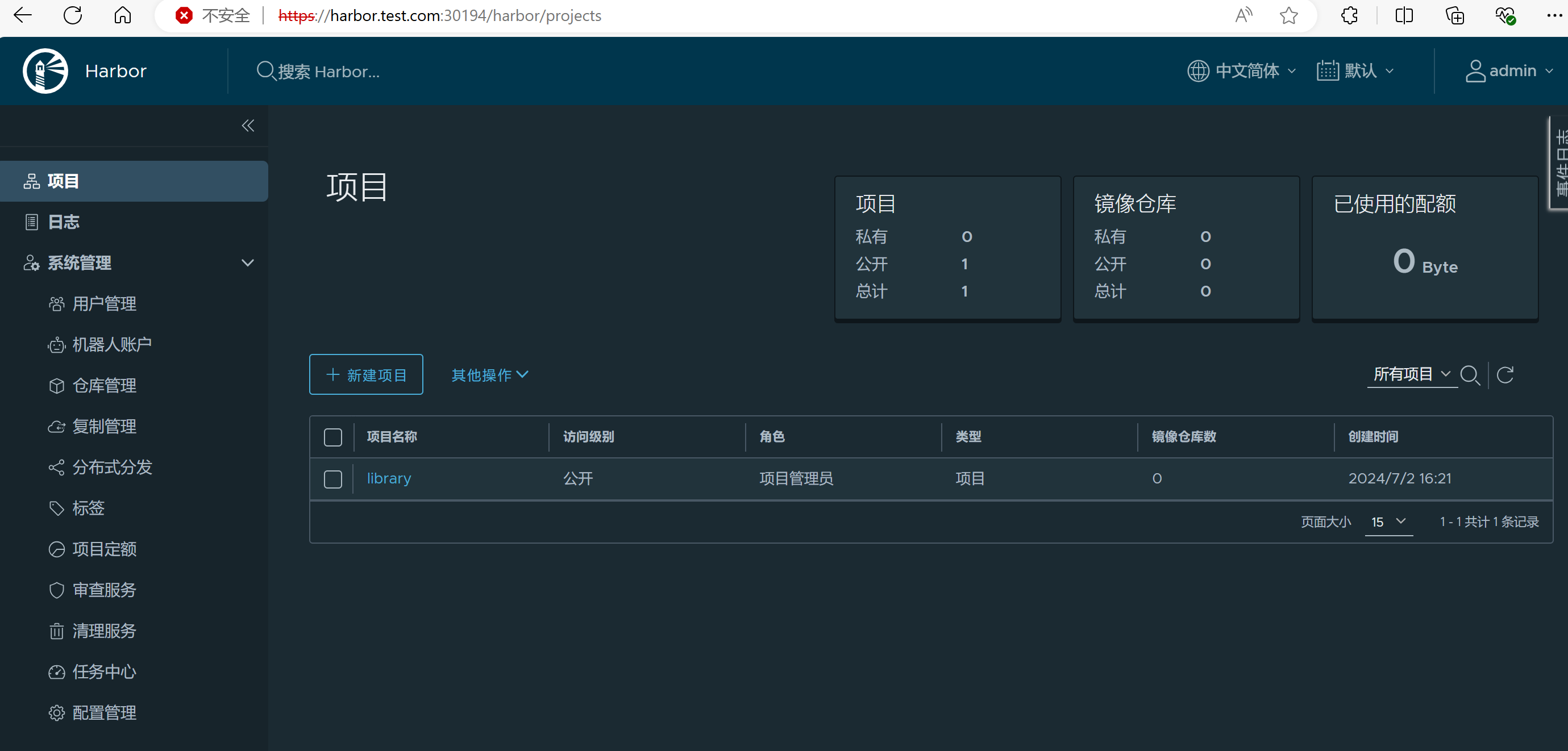
NAME CLASS HOSTS ADDRESS PORTS AGE
harbor-ingress nginx harbor.test.com 10.102.230.242 80, 443 7m9s
客戶端訪問測試,在客戶端配置域名解析,harbor.test.com解析到ingress-nginx節點IP,訪問https://harbor.test.com:30194:

使用者名稱admin,密碼Harbor12345
部署harbor--NodePort方式暴露服務
上述使用ingress方式部署依賴nginx-ingress控制器,如果為了簡化部署,可以使用NodePort方式:
export node_ip=192.168.0.61
helm upgrade --install harbor harbor/harbor --namespace harbor --create-namespace \
--set expose.type=nodePort \
--set expose.tls.auto.commonName=$node_ip \
--set externalURL='https://$node_ip:31234'
--set harborAdminPassword="Harbor12345" \
--set persistence.persistentVolumeClaim.registry.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.jobservice.jobLog.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.database.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.redis.storageClass="openebs-hostpath" \
--set persistence.persistentVolumeClaim.trivy.storageClass="openebs-hostpath"
透過https://$node_ip:31234直接訪問harbor。
客戶端上傳映象驗證
- 到處ca證書
kubectl -n harbor get secrets harbor-ingress -o jsonpath="{.data.ca\.crt}" | base64 -d >ca.crt
- 複製ca.crt到docker客戶端所在機器
docker執行時和客戶端:
root@ubuntu:~# mkdir -p /etc/docker/certs.d/harbor.test.com:30194/
root@ubuntu:~# ls /etc/docker/certs.d/harbor.test.com:30194/
ca.crt
如果使用containerd,配置類似:
root@ubuntu:~# mkdir -p /etc/containerd/certs.d/harbor.test.com:30194/
root@ubuntu:~# ls /etc/containerd/certs.d/harbor.test.com:30194/
ca.crt
- 配置解析
echo "192.168.0.62 harbor.test.com" >>/etc/hosts
- 測試登入
root@ubuntu:~# docker login -u admin -p Harbor12345 https://harbor.test.com:30194
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /home/test/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
- 推送映象
root@ubuntu:~# docker push harbor.test.com:30194/library/kubemark:1.19.0
The push refers to repository [harbor.test.com:30194/library/kubemark]
c746c8a16e15: Pushed
f47163e8de57: Pushed
0d1435bd79e4: Pushed
1.19.0: digest: sha256:95effc616f84c0c3d3645ee489f57ec635002bcf5eec1f0892936f485110d529 size: 949
參考資料
-
https://github.com/goharbor/harbor-helm
-
https://goharbor.io/docs/2.5.0/install-config/harbor-ha-helm/
-
https://blog.csdn.net/networken/article/details/126295863