ORACLE ORA600之SQL隱碼攻擊一
2016年第一季度某平臺的巡檢中,在oracle資料庫的告警日誌中發現如下報錯:
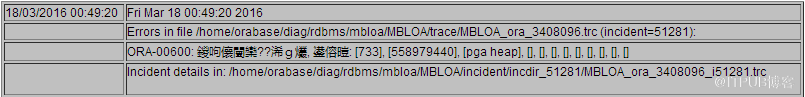
根據告警資訊檢視相關的trc檔案:
Trace file /home/orabase/diag/rdbms/****/****/trace/****_ora_3408096.trc
Oracle Database 11g Enterprise Edition Release 11.2.0.3.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
ORACLE_HOME = /home/orabase/product/db/11203
System name: AIX
Node name: ****
Release: 1
Version: 6
Machine: *********
Instance name: ****
Redo thread mounted by this instance: 1
Oracle process number: 266
Unix process pid: 3408096, image: oracle@****
*** 2016-03-18 00:49:20.826
*** SESSION ID:(1977.61609) 2016-03-18 00:49:20.826
*** CLIENT ID:() 2016-03-18 00:49:20.826
*** SERVICE NAME:(SYS$USERS) 2016-03-18 00:49:20.826
*** MODULE NAME:() 2016-03-18 00:49:20.826
*** ACTION NAME:() 2016-03-18 00:49:20.826
Incident 51281 created, dump file: /home/orabase/diag/rdbms/****/****/incident/incdir_51281/****_ora_3408096_i51281.trc
ORA-00600: 內部錯誤程式碼, 引數: [733], [558979440], [pga heap], [], [], [], [], [], [], [], [], []
再檢視****_ora_3408096_i51281.trc資訊如下:
*** 2016-03-18 00:49:20.842
*** SESSION ID:(1977.61609) 2016-03-18 00:49:20.842
*** CLIENT ID:() 2016-03-18 00:49:20.842
*** SERVICE NAME:(SYS$USERS) 2016-03-18 00:49:20.842
*** MODULE NAME:() 2016-03-18 00:49:20.842
*** ACTION NAME:() 2016-03-18 00:49:20.842
Dump continued from file: /home/orabase/diag/rdbms/****/****/trace/****_ora_3408096.trc
ORA-00600: 內部錯誤程式碼, 引數:[733], [558979440], [pga heap], [], [], [], [], [], [], [], [], []
========= Dump for incident 51281 (ORA 600 [733]) ========
*** 2016-03-18 00:49:20.862
dbkedDefDump(): Starting incident default dumps (flags=0x2, level=3, mask=0x0)
----- Current SQL Statement for this session (sql_id=4dgy5ydm4qux1) -----
select ENTERPRISEID,STATUS from ENTERPRISE_INFO e where e.ENTERPRISECODE='-8838' OR 4914=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(112)||CHR(118)||CHR(98)||CHR(113)||(SELECT (CASE WHEN (4914=4914) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(98)||CHR(118)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL) AND 'eCHY'='eCHY'
在****_ora_3408096.trc發現有SQL語句如下:
select ENTERPRISEID,STATUS from ENTERPRISE_INFO e where e.ENTERPRISECODE='-8838' OR 4914=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(112)||CHR(118)||CHR(98)||CHR(113)||(SELECT (CASE WHEN (4914=4914) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(98)||CHR(118)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL) AND 'eCHY'='eCHY'
該SQL語句是典型的Oracle AND error-based的SQL隱碼攻擊,相關修復方法就是對SQL語句引數進行校驗過濾,資料庫系統進行安全掃描並進行漏洞修復。

根據告警資訊檢視相關的trc檔案:
Trace file /home/orabase/diag/rdbms/****/****/trace/****_ora_3408096.trc
Oracle Database 11g Enterprise Edition Release 11.2.0.3.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
ORACLE_HOME = /home/orabase/product/db/11203
System name: AIX
Node name: ****
Release: 1
Version: 6
Machine: *********
Instance name: ****
Redo thread mounted by this instance: 1
Oracle process number: 266
Unix process pid: 3408096, image: oracle@****
*** 2016-03-18 00:49:20.826
*** SESSION ID:(1977.61609) 2016-03-18 00:49:20.826
*** CLIENT ID:() 2016-03-18 00:49:20.826
*** SERVICE NAME:(SYS$USERS) 2016-03-18 00:49:20.826
*** MODULE NAME:() 2016-03-18 00:49:20.826
*** ACTION NAME:() 2016-03-18 00:49:20.826
Incident 51281 created, dump file: /home/orabase/diag/rdbms/****/****/incident/incdir_51281/****_ora_3408096_i51281.trc
ORA-00600: 內部錯誤程式碼, 引數: [733], [558979440], [pga heap], [], [], [], [], [], [], [], [], []
再檢視****_ora_3408096_i51281.trc資訊如下:
*** 2016-03-18 00:49:20.842
*** SESSION ID:(1977.61609) 2016-03-18 00:49:20.842
*** CLIENT ID:() 2016-03-18 00:49:20.842
*** SERVICE NAME:(SYS$USERS) 2016-03-18 00:49:20.842
*** MODULE NAME:() 2016-03-18 00:49:20.842
*** ACTION NAME:() 2016-03-18 00:49:20.842
Dump continued from file: /home/orabase/diag/rdbms/****/****/trace/****_ora_3408096.trc
ORA-00600: 內部錯誤程式碼, 引數:[733], [558979440], [pga heap], [], [], [], [], [], [], [], [], []
========= Dump for incident 51281 (ORA 600 [733]) ========
*** 2016-03-18 00:49:20.862
dbkedDefDump(): Starting incident default dumps (flags=0x2, level=3, mask=0x0)
----- Current SQL Statement for this session (sql_id=4dgy5ydm4qux1) -----
select ENTERPRISEID,STATUS from ENTERPRISE_INFO e where e.ENTERPRISECODE='-8838' OR 4914=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(112)||CHR(118)||CHR(98)||CHR(113)||(SELECT (CASE WHEN (4914=4914) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(98)||CHR(118)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL) AND 'eCHY'='eCHY'
在****_ora_3408096.trc發現有SQL語句如下:
select ENTERPRISEID,STATUS from ENTERPRISE_INFO e where e.ENTERPRISECODE='-8838' OR 4914=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(112)||CHR(118)||CHR(98)||CHR(113)||(SELECT (CASE WHEN (4914=4914) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(98)||CHR(118)||CHR(118)||CHR(113)||CHR(62))) FROM DUAL) AND 'eCHY'='eCHY'
該SQL語句是典型的Oracle AND error-based的SQL隱碼攻擊,相關修復方法就是對SQL語句引數進行校驗過濾,資料庫系統進行安全掃描並進行漏洞修復。
來自 “ ITPUB部落格 ” ,連結:http://blog.itpub.net/29357786/viewspace-2061683/,如需轉載,請註明出處,否則將追究法律責任。
相關文章
- SQL隱碼攻擊(一)SQL
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊SQL
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊-SQL隱碼攻擊技術-語句注入SQL
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊-SQL隱碼攻擊技術-語句修改SQL
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊-防衛SQL隱碼攻擊-驗證檢查SQL
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊-防衛SQL隱碼攻擊-繫結變數SQL變數
- Oracle SQL隱碼攻擊 總結OracleSQL
- SQL隱碼攻擊SQL
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊-防衛SQL隱碼攻擊-顯式格式化模型SQL模型
- 反恐精英之動態SQL和SQL隱碼攻擊-SQL隱碼攻擊-SQL隱碼攻擊技術-資料型別轉換SQL資料型別
- WAF攻防之SQL隱碼攻擊篇SQL
- 【SQL Server】--SQL隱碼攻擊SQLServer
- MYSQL SQL隱碼攻擊MySql
- 【SQL隱碼攻擊原理】SQL
- 防止SQL隱碼攻擊SQL
- SQL隱碼攻擊(pikachu)SQL
- SQL隱碼攻擊方法SQL
- WEB三大攻擊之—SQL隱碼攻擊與防護WebSQL
- SQL隱碼攻擊原理是什麼?如何防範SQL隱碼攻擊?SQL
- Java審計之SQL隱碼攻擊篇JavaSQL
- SQL隱碼攻擊式攻擊掃描器SQL
- SQL隱碼攻擊語句SQL
- pikachu-SQL隱碼攻擊SQL
- SQL隱碼攻擊導圖SQL
- SQL隱碼攻擊問題SQL
- SQL隱碼攻擊的例子SQL
- ZMLCMS-SQL隱碼攻擊SQL
- SQL隱碼攻擊演練SQL
- 預防SQL隱碼攻擊SQL
- SQL隱碼攻擊總結SQL
- SQL隱碼攻擊原理及程式碼分析(一)SQL
- 軟體安全測試之SQL隱碼攻擊SQL
- DVWA-SQL Injection(SQL隱碼攻擊)SQL
- 攻擊JavaWeb應用[3]-SQL隱碼攻擊[1]JavaWebSQL
- 攻擊JavaWeb應用[4]-SQL隱碼攻擊[2]JavaWebSQL
- 【網路安全】什麼是SQL隱碼攻擊漏洞?SQL隱碼攻擊的特點!SQL
- SQL隱碼攻擊關聯分析SQL
- SQL隱碼攻擊-堆疊注入SQL