VPC網路ECS搭建L2TPVPN
本文,主要介紹如何在 VPC 網路環境的 ECS 下搭建 L2TP VPN。
環境說明
1、Server 端使用 Centos 6 系統部署
2、客戶端使用 Windows 7 撥號
3、環境軟體包 openswan ppp xl2tpd
Server 端部署
1、安裝環境包
[root@l2tp ~]# yum install -y make gcc gmp-devel xmlto bison flex xmlto libpcap-devel vim-enhanced policycoreutils
2、安裝軟體包
[root@l2tp ~]# yum install -y openswan ppp xl2tpd
3、在 /etc/sysctl.conf 新增如下內容
`net.ipv4.ip_forward = 1
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.log_martians = 0
net.ipv4.conf.default.log_martians = 0
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.icmp_ignore_bogus_error_responses = 1`
然後使用 sysctl -p 讓配置的引數生效。
4、編輯 /etc/ipsec.conf
`config setup
protostack=netkey
dumpdir=/var/run/pluto/ virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10include /etc/ipsec.d/*.conf
conn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNATconn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=0.0.0.0
leftprotoport=17/1701
right=%any
rightprotoport=17/%any`
5、編輯 /etc/ipsec.secrets
`include /etc/ipsec.d/*.secrets
public_ip %any: PSK “YourPsk”`
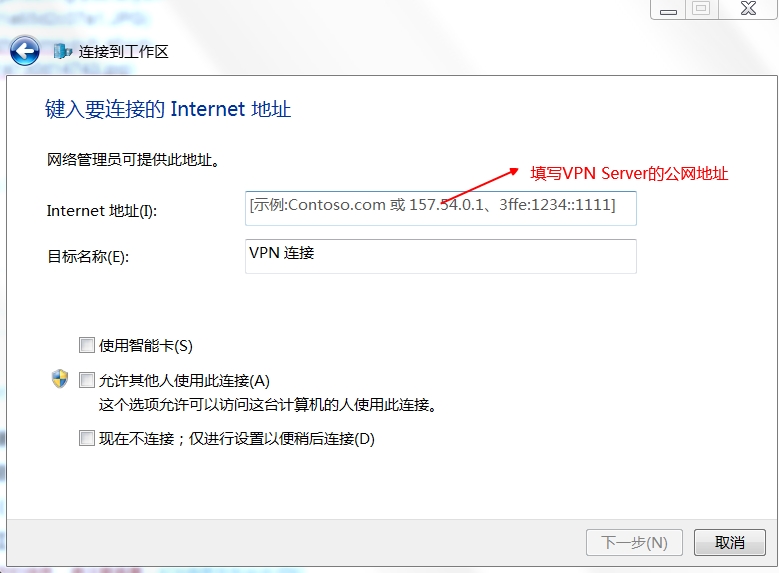
public_ip 是 ECS 公網 IP 或者是繫結的 EIP
YourPsk 為預共享金鑰。
6、驗證 ipsec 執行狀態
[root@l2tp ~]# ipsec verifyVerifying installed system and configuration files
Version check and ipsec on-path [OK]Libreswan 3.15 (netkey) on 2.6.32-696.3.2.el6.x86_64Checking for IPsec support in kernel [OK]NETKEY: Testing XFRM related proc values
` ICMP default/send_redirects [OK]`
`ICMP default/accept_redirects [OK]`
`XFRM larval drop [OK]`Pluto ipsec.conf syntax [OK]Hardware random device [N/A]Checking rp_filter [OK]Checking that pluto is running [OK] Pluto listening for IKE on udp 500 [OK]Pluto listening for IKE/NAT-T on udp 4500 [OK]Pluto ipsec.secret syntax [OK]Checking `ip` command [OK]Checking `iptables` command [OK]Checking `prelink` command does not interfere with FIPSChecking for obsolete ipsec.conf options [OK]Opportunistic Encryption [DISABLED]
沒有出現錯誤說明 IPSEC 配置正確。
7、編輯 /etc/xl2tpd/xl2tpd.conf
`[global]
ipsec saref = yes
[lns default]
ip range = 192.168.1.128-192.168.1.254
local ip = 0.0.0.0
require chap = yes
refuse pap = yes
require authentication = yes
name = LinuxVPNserver
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes`
8、配置使用者名稱和密碼,編輯 /etc/ppp/chap-secrets
# Secrets for authentication using CHAP# client server secret IP addressesusername l2tpd userpass *
9、重新啟動 ipsec 和 xl2tp
`[root@l2tp ~]# service ipsec restart
[root@l2tp ~]# service xl2tp restart`
客戶端配置
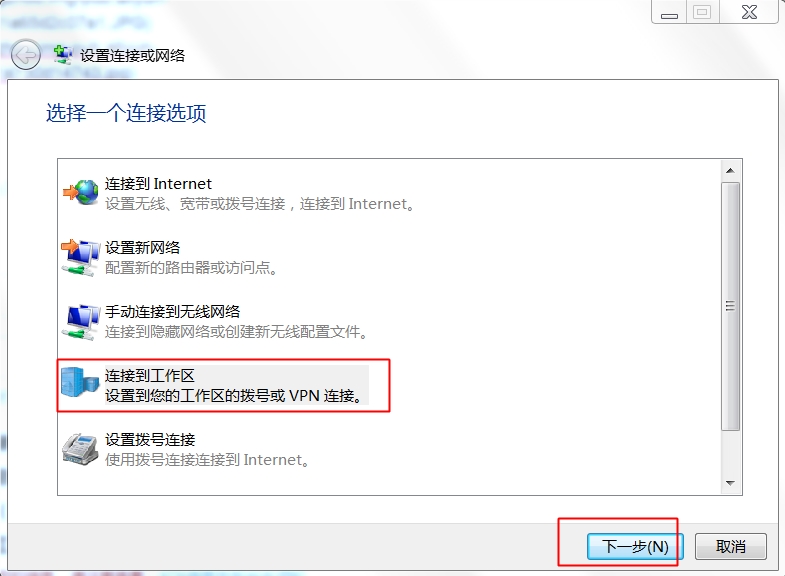
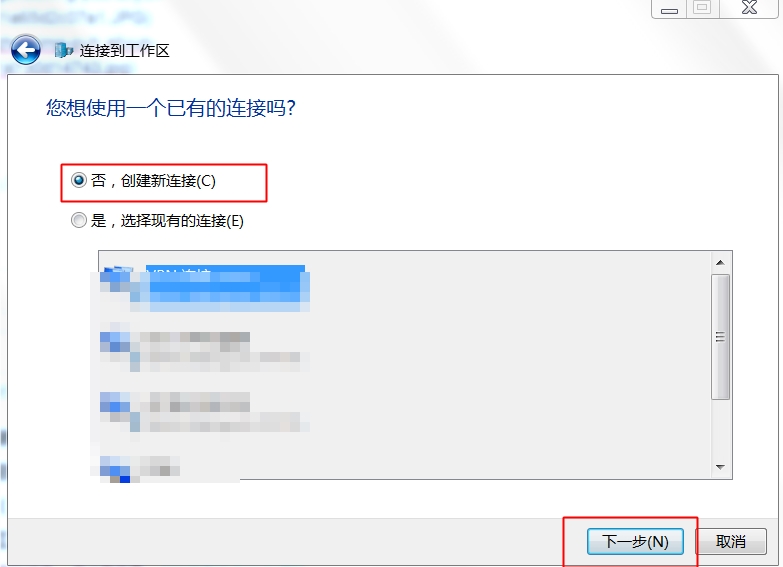
1、建立撥號連線
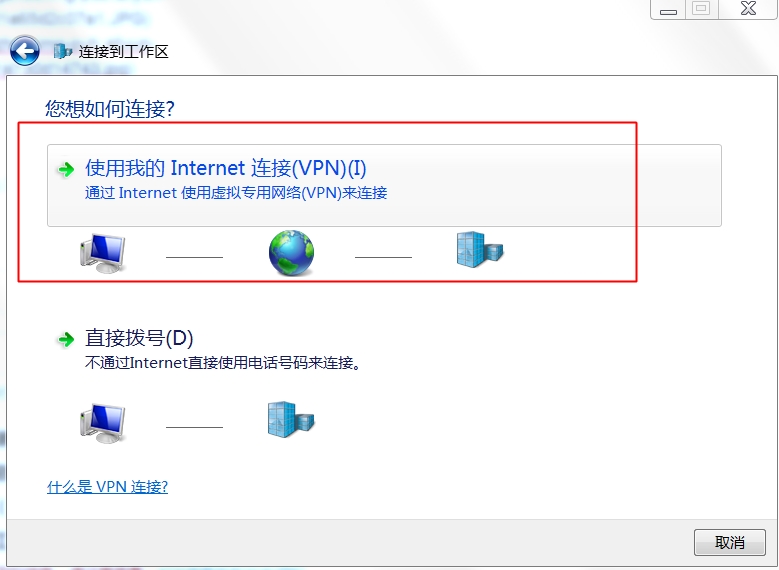
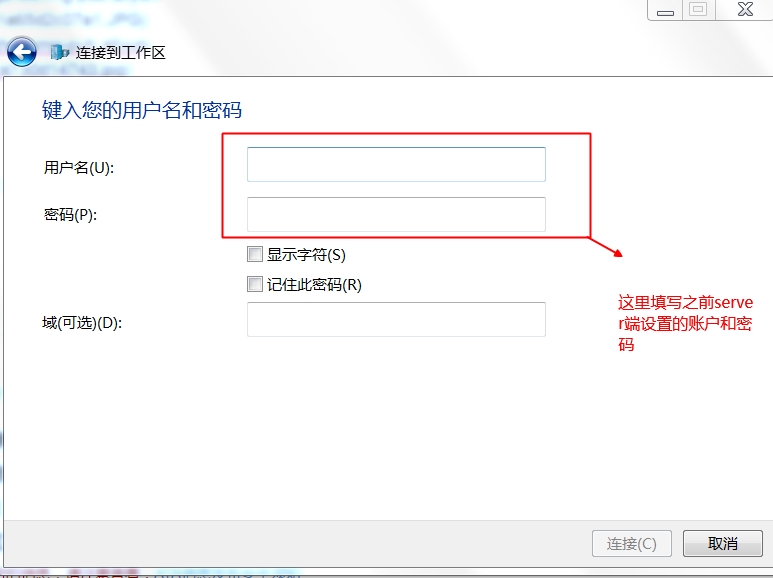
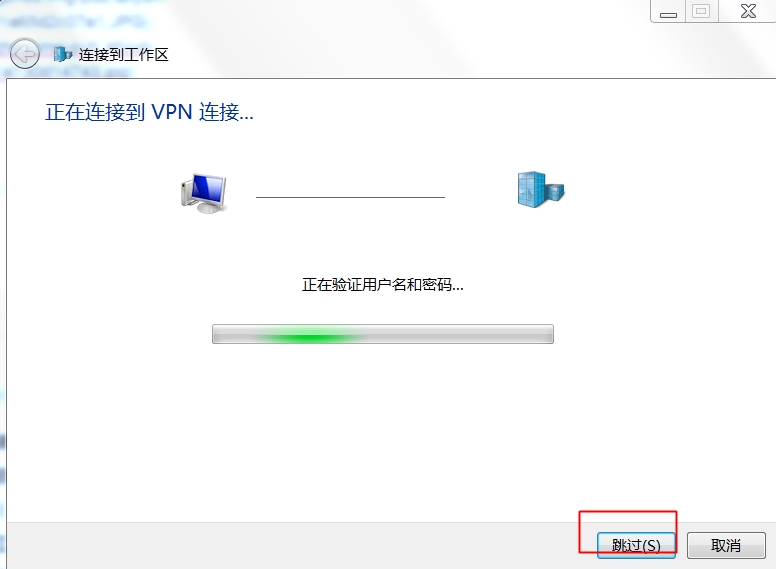
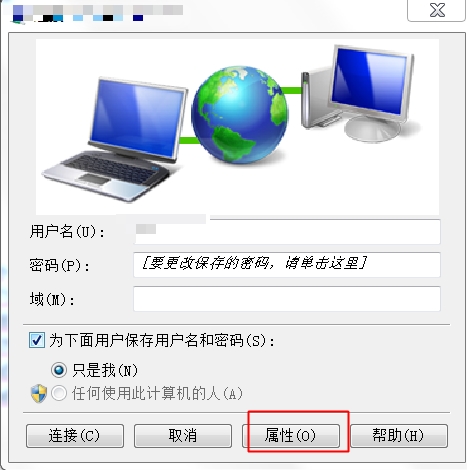
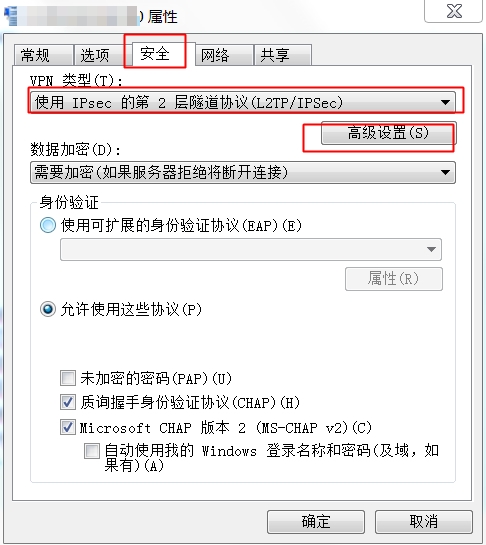
2、設定使用二層隧道加密
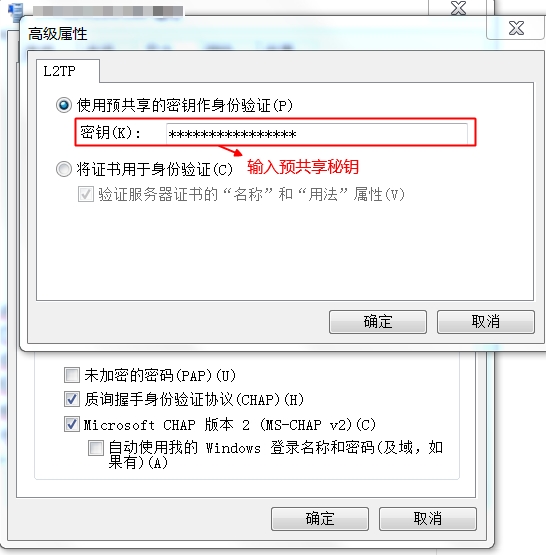
撥號成功後在 Server 端會多出一個 ppp0 的網路卡: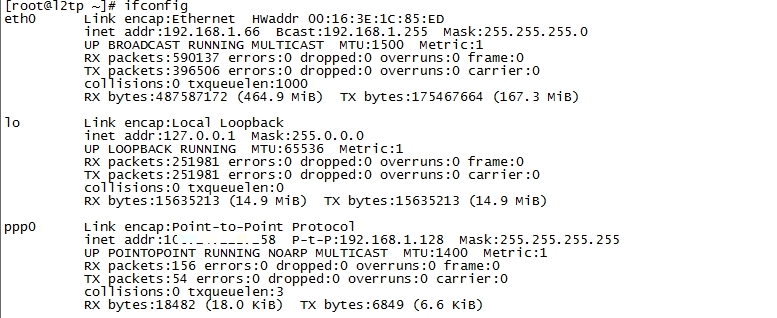
相關文章
- ECS的VPC服務授權
- OPPO雲VPC網路實踐
- 在滴滴雲 VPC 內搭建內網 DNS 服務內網DNS
- 使用ECS和OSS搭建個人網盤
- 解決阿里雲VPC網路下面ECS不能指定高於X.X.X.247私有IP地址的方法阿里
- 基於ECS和NAS搭建個人網盤
- 什麼是阿里雲vpc專用網路?阿里
- 【AWS】通過對等網路打通VPC訪問
- 一張圖看懂阿里雲網路產品[二] 專有網路VPC阿里
- 使用PolarDB和ECS搭建入口網站網站
- CCE叢集VPC網路模式下幾種訪問場景模式
- VPC最佳實踐(六):業務如何從經典網路平滑遷移到VPC
- 使用PolarDB和ECS搭建入口網站(阿里雲)網站阿里
- 阿里雲伺服器ECS搭建網站詳細教程阿里伺服器網站
- ECS雲伺服器搭建Mysql,並提供公網連線伺服器MySql
- 香港地域ECS網路延遲異常通知公告
- 基於ECS搭建雲上部落格
- 基於ECS快速搭建Docker環境Docker
- 基於ECS搭建GitLab服務Gitlab
- VPC最佳實踐(四):VPC中的訪問控制
- 如何搭建“網路課堂”
- 基於ECS搭建FTP服務(阿里雲)FTP阿里
- DevOpsSOP 基於阿里雲VPC搭建Storm+Kafka+Zookeeper叢集dev阿里ORMKafka
- pytorch——VGG網路搭建PyTorch
- 使用Vmware搭建虛擬網路
- 網路搭建的基本流程包括
- 如何解決公網無法訪問阿里雲ECS搭建的MongoDB服務阿里MongoDB
- Day2——基於ECS快速搭建Docker環境Docker
- 在ECS上輕鬆搭建RDS的從例項
- 阿里雲 VPC 內網效能測試最佳實踐阿里內網
- 會議WiFi網路租賃,臨時網路租賃,展會網路搭建WiFi
- 貝聊VPC遷移
- 阿里雲618有獎體驗:使用PolarDB和ECS搭建入口網站阿里網站
- SSL連線,搭建網路安全道路
- 【機器學習】搭建神經網路筆記機器學習神經網路筆記
- 商企網路拓撲的搭建
- 網路拓撲—FTP服務搭建FTP
- VPC內網服務可用性監控最佳實踐內網